11 minutes
Anonymous Avatars: Enhancing Privacy with Anonymized Profile Pictures

In today’s digital age, maintaining privacy while participating in social media can be challenging, especially for professionals on platforms like LinkedIn where a profile picture is often essential. The primary concern revolves around facial recognition technologies that can compromise privacy without our consent.
TL;DR: Skip to 2 Key Strategies for Safeguarding Your Public Profile Pictures
Dangers of Publishing Photos Online
Publishing pictures online can expose individuals to several potential dangers, including:
Loss of privacy: When you publish a photo online, whether on social media, a blog, or any other website, you are essentially giving up control over who can see and access that photo. Even if you use privacy settings to restrict access, there’s always the possibility that someone could screenshot the image, save it, and share it elsewhere. Once a photo is on the internet, it can be very difficult, if not impossible, to completely remove it. This means that photos you share online could potentially be viewed by anyone, including strangers, employers, or people you may not want to see them, both now and in the future.Misuse by others: When you put a photo online, you are also opening it up to potential misuse by others. People can easily download your photos, alter them using editing software, and then reshare them in different contexts without your consent. For example, someone could take a photo of you and turn it into a meme, use it to create a fake social media profile, or even incorporate it into inappropriate or malicious content. This can be particularly distressing if the altered photo is embarrassing, offensive, or damaging to your reputation.Reputational damage: The photos you share online can have a significant impact on your personal and professional reputation. Inappropriate, embarrassing, or controversial photos, even if they are old or taken out of context, could potentially damage your reputation and have consequences in your personal and work life. For example, many employers now routinely check the online presence of potential hires, and photos that show you in a negative light could hurt your chances of getting a job. Similarly, photos could affect your relationships or even your standing in your community.Cyberbullying: Unfortunately, photos shared online can also be used as a tool for cyberbullying. People can use your photos to mock, harass, intimidate, or bully you online, leaving hurtful comments or sharing the photos in a way intended to embarrass or humiliate you. This can be particularly harmful for children and teenagers, who may be more vulnerable to the emotional impact of cyberbullying.Metadata concerns: When you take a photo with a digital camera or smartphone, the image file often includes metadata - additional information about the photo such as the date and time it was taken, the camera settings used, and even the GPS coordinates of where the photo was captured. When you share a photo online, this metadata is often included with the image file. This means that photos can potentially reveal sensitive information about your location, your habits, and your activities that you may not want to share publicly.Facial recognition: With the increasing sophistication of facial recognition technology, photos of your face that you share online could potentially be used to identify and track you across different platforms and databases. This means that your online photos could be used to connect different aspects of your online presence, even if you use different names or identities on different sites. Facial recognition technology is becoming more widely used by companies, governments, and law enforcement, raising concerns about privacy and surveillance.Attracting stalkers: The photos you share online can also potentially attract unwanted attention from stalkers or other malicious individuals. Photos can reveal a lot of personal information about you, such as where you live, where you work, who your friends and family are, and what activities you engage in. A stalker could use this information to track your movements, learn your routines, and even attempt to contact or harass you or your loved ones.Scams and phishing: Scammers and fraudsters can also use your photos for malicious purposes. They might use your photo to create a fake identity, posing as you in order to trick your friends and contacts into giving up sensitive information or money. For example, a scammer could use your photo to create a fake social media profile and then reach out to your friends with a phishing message that appears to come from you. Alternatively, scammers could use your photo in fake online dating profiles or other scams to lure in victims.
Given all these potential risks, it’s important to be very cautious and selective about the photos you choose to share online. Before posting a photo, consider whether you would be comfortable with that photo being public and permanent. Use privacy settings to limit who can see your photos, and be particularly cautious about sharing photos that reveal sensitive information or that could be embarrassing or damaging if taken out of context. Watermarking your photos can also help deter misuse, as it makes it more difficult for people to use your photos without attribution. Ultimately, a little caution and forethought when sharing photos online can go a long way in protecting your privacy and security.
💁 Assume anything you upload online can never be deleted and may leak at any time. Stay safe.
Dangers of Facial Recognition
Here are some of the main dangers and concerns around facial recognition technology:
Privacy violations: Facial recognition technology poses significant threats to individual privacy. It enables the mass surveillance and tracking of individuals without their knowledge or consent. Cameras equipped with facial recognition can be used to identify and track people as they move through public spaces, such as streets, parks, and shopping centers. Online, facial recognition can be used to identify individuals in photos and videos posted to social media or other websites. This means that people can be identified and tracked across both physical and digital spaces, creating a comprehensive record of their movements and activities. This level of surveillance is a major violation of personal privacy and can have a chilling effect on free speech and association.Bias and inaccuracy: Many facial recognition systems have been shown to exhibit significant bias based on factors such as race, gender, and age. Studies have consistently found that these systems have higher error rates when attempting to identify people of color, particularly women of color, as well as individuals at the extremes of the age spectrum (very young or very old). This bias can lead to false identifications, where innocent individuals are mistakenly flagged as criminals or persons of interest. In a law enforcement context, this could lead to wrongful arrests or harassment. In commercial applications, it could result in individuals being denied access to services or subjected to additional scrutiny. The bias inherent in many facial recognition systems raises serious concerns about their fairness and reliability.Misuse by authorities: The power of facial recognition technology in the hands of law enforcement and government agencies raises significant concerns about potential misuse. Authorities could use this technology to target specific individuals or groups based on factors such as race, ethnicity, religion, or political beliefs. For example, facial recognition could be used to identify and track protesters at a peaceful demonstration, which could then be used to harass or intimidate those individuals. Governments could also use facial recognition to exceed legal limits on surveillance, such as by using it to monitor individuals without probable cause or a warrant. In countries with authoritarian regimes, facial recognition could be a powerful tool for suppressing dissent and maintaining control over the population.Data security risks: Facial recognition systems require the collection and storage of massive amounts of sensitive biometric data in the form of digital face templates or images. This data is highly personal and cannot be changed if compromised, unlike passwords or credit card numbers. If facial recognition databases are not properly secured, they could be vulnerable to hacking, data breaches, or insider threats. In the wrong hands, this data could be used for identity theft, blackmail, or other nefarious purposes. Even if not maliciously misused, the centralized collection of face data creates a honeypot that could be targeted by cybercriminals. Robust security measures and strict limits on data retention are critical for protecting individuals’ face data.Lack of regulation: Despite the rapid proliferation of facial recognition technology, its use remains largely unregulated in many jurisdictions around the world. There are often few or no legal constraints on how the technology can be deployed, what data can be collected and retained, or how that data can be used or shared. This regulatory gap leaves individuals vulnerable to privacy violations and abuse. There is an urgent need for comprehensive laws and regulations governing the use of facial recognition. These should include requirements for consent, transparency, data minimization, accuracy testing, and independent oversight. Without such safeguards, the risks of facial recognition are likely to continue growing unchecked.Inability to opt-out: In many contexts where facial recognition is deployed, individuals have no ability to opt-out or control how their biometric data is collected and used. For example, if facial recognition cameras are installed in a public space, individuals passing through that space have no choice but to have their faces scanned and analyzed. Similarly, if a social media platform uses facial recognition to identify individuals in posted photos, users may not have the ability to prevent their biometric data from being collected and associated with their account. This lack of control over one’s own biometric data is a significant violation of personal autonomy and privacy. Individuals should have the right to decide whether and how their face data is used.Chilling effects: The widespread use of facial recognition, particularly in public spaces, can have a significant chilling effect on free speech, assembly, and association. If people know that they are being constantly monitored and identified, they may be less likely to engage in activities that are seen as controversial or politically sensitive. For example, individuals may be hesitant to attend a protest or rally if they know that their presence will be recorded and linked to their identity. This could stifle public discourse and civic engagement. Even if facial recognition data is not actively being used to target individuals, the mere knowledge of its collection can alter behavior in ways that undermine democratic values and individual liberty.
The risks posed by facial recognition technology are significant and multifaceted, ranging from privacy violations and bias to security threats and chilling effects on free expression. As the technology continues to advance and become more widely deployed, it is critical that policymakers, regulators, and society as a whole grapple with these risks and implement strong safeguards to protect individual rights. This may include measures such as requiring warrants for law enforcement use, mandating accuracy testing and bias audits, giving individuals the right to opt-out, and placing strict limits on data collection and retention. Only by proactively addressing the dangers of facial recognition can we hope to harness its benefits while protecting against its most pernicious harms.
💁 It’s important to be mindful of privacy settings, the audience, and the potential implications when sharing photos online.
Mitigation
Balancing Privacy and Professionalism: 2 Key Strategies for Safeguarding Your Public Profile Pictures
1. Using Generative AI to Create Privacy-Preserving Profile Pictures
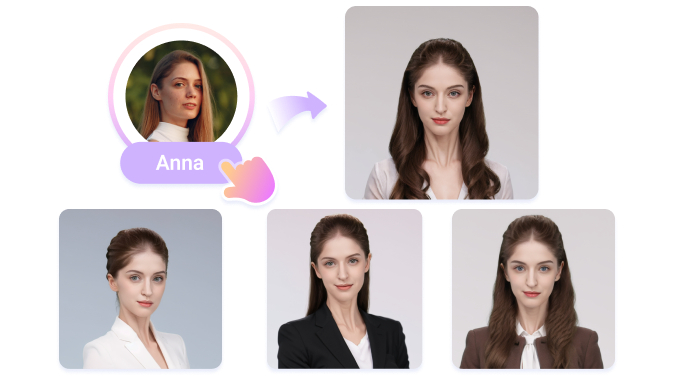
Primary straightforward solution is to use generative AI to create profile pictures that resemble you without being your exact likeness. Numerous online tools, such as “LinkedIn Profile Maker,” can generate professional-looking profile images that maintain your anonymity. Simply search for these tools and select one that meets your needs.
By leveraging these methods, you can balance the need for a professional online presence with the imperative of personal privacy.
2. Fawkes

Fawkes is an innovative algorithm and software tool that empowers individuals to protect their privacy by disrupting facial recognition models. Running locally on your computer, Fawkes makes subtle, pixel-level changes to your photos—changes that are imperceptible to the human eye. This process, known as image cloaking, “poisons” facial recognition models by teaching them a distorted version of your facial features. Consequently, when someone attempts to use these modified images to build a facial recognition model, the model will fail to accurately recognize you from unaltered photos. This tool provides a robust layer of privacy while allowing you to share your photos as usual on social media, print them, or display them on digital devices.
Fawkes is a tool designed to prevent third parties from using your photos to build accurate facial recognition models of you. It works by cloaking your images in a way that makes them unusable for model training.
However, it’s important to understand what Fawkes does and does not do. Fawkes is not designed to protect the specific images you apply the cloak to. If someone already has a facial recognition model trained on your real, uncloaked images (e.g., Facebook or Pimeyes), they may still be able to recognize you in cloaked photos.
Instead, Fawkes is designed to prevent a third party from building an accurate recognition model of you using your cloaked photos. By cloaking your images before sharing them online, you ensure that anyone attempting to train a model using those photos will end up with an incorrect representation of your face. As a result, their model would fail to correctly identify you in real, uncloaked photos.
In summary, Fawkes is a valuable tool for protecting your privacy from unauthorized facial recognition model training. While it may not prevent recognition by existing models, it can help you maintain control over your digital identity and prevent the creation of new, accurate models without your consent.
Stay curious, stay ethical, and keep exploring!
anonimity privacy socialmedia linkedin fawkes ai cybersecurity privacy facialrecognition
2289 Words
2024-05-24 15:51 (Last updated: 2024-05-24 18:58)
c33dd89 @ 2024-05-24